Advanced Malware Removal on Windows Devices
- Jan 20, 2018
- 6 min read

As a disclaimer to this article, the best method of response to any malware incident is simply to wipe and reload the machine in question. Due to this, redundant and reliable backups are incredibly important to both businesses and home users. There may, however, be scenarios where a factory reset is not an option or is simply not necessary. This guide aims to assist those looking to stop the propagation of an infection and remove potentially unwanted programs from their devices.
There are a number of tools I generally use to fight malicious programs as well as simply remove PUPs and free up system resources on client computers. Though they can all be downloaded individually from their respective authors’ sites, I prefer to get them all from Bleeping Computer (with the exception of Process Explorer and Autoruns):
ProcEx
Autoruns
RKill – I recommend downloading the version called iExplore
JRT
Adwcleaner
MBAR
FRST
I strongly advise running all of these as Administrator when it comes time to do so.
None of these applications need to be formally installed on the host. I typically keep these, as well as all my troubleshooting tools, on a write-protected USB drive. This is especially useful when the malware you’re dealing with spreads through admin shares or other means and requires remediation to be done offline.
In our scenario, I’ve downloaded this generous application that updates all of my drivers for me. While that’s a very kind thing for it to claim to do, we don’t want this application and will be removing it:

The first step in any incident response is to stop propagation – that is to kill the spread of infection. The best way to do this is to remove the infected device from the network or, if that’s not an option, disable all admin shares. I won’t explain how to do so in this article, though more information can be found here. Anti-malware vendors, like Webroot, also offer scripts that perform this task. If you suspect a trojan is installed on your machine, you can use the command netstat -an in cmd to see if there are any open ports on your machine, as well as the associated IP address that is listening:

In this screenshot, the address on the left is the local IP of the virtual machine in my lab. On the right are any external IP addresses as well as the ports they’re listening in on. These appear because I had a browser window opened to Google.
If I want to dig deeper as to what programs are running in the background I’ll proceed to use Process Explorer and Autoruns. These are Sysinternals tools used for general troubleshooting, however this video demonstrates how effective they can be in spotting malware. Utilizing Autoruns, we are able to see the autorun entry for everything on our system.

Here we find that our unwanted program is set to start up as soon as we boot into Windows. By right clicking this item we can perform a number of actions, such as jump to its entry in Task Scheduler or submit its hash to VirusTotal. As we can see here, there are multiple antivirus engines that flag it as malicious or otherwise unwanted. We can also very simply delete the task right from Autoruns. ProcEx performs in a similar fashion but monitors all system processes running in real time. Essentially like a beefed-up task manager, we can see the name of the executable file, it’s system drain and its publisher. Any application without a verified signature from reputable source is worthy of investigation Right-clicking a questionable process again grants us a number of options:

If there are multiple instances of an application, or many unwanted applications running, we can suspend all of them. This is recommended over “Kill Process” because many intelligent variants of malware detect when it’s being killed or removed and will replicate upon doing so. Once it’s suspended, we can continue with our remediation. As shown above, we also have the options to send hashes to VirusTotal and, under Properties, verify a program’s signature. This is relevant for a number of reasons but, for example, if you have a program called “Task Manager” running in the background but it’s not signed by Microsoft we can probably determine that it is malware.

One last nifty function of ProcEx is its ability to snap to a running process using the Crosshair function along the top toolbar. Just drag and drop the icon to something running on your desktop and ProcEx will show you what it is:
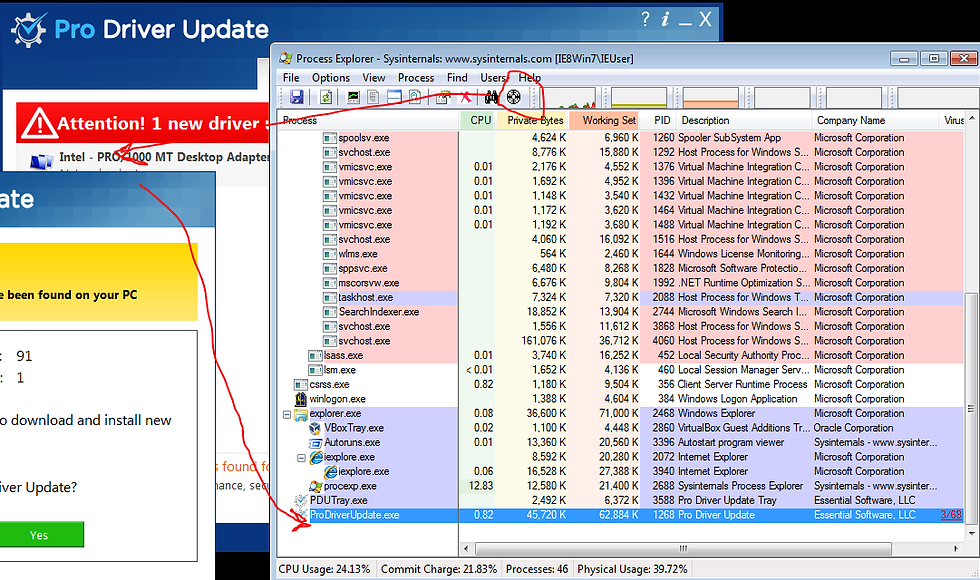
Once we suspend ProDriverUpdate, we’ll see that it has a heart attack right there on our desktop:

The majority of the tools left in our list are basically point-and-click and they’ll do the rest of the work for us. To begin, start up your iExplore and let it run entirely. It will search for a number of things including malicious programs, proxy settings, questionable registry entries and modifications to your host file. It’s kind enough to make a backup of your registry prior to ripping anything out. It will also spit out a text log of its findings:

Next we can spin up MBAR, JRT and Adwcleaner. They search for all manner of PUPs but are unique enough in their functions that running them all is beneficial. JRT will also attempt to create a restore point prior to executing:

Last up is FRST, which we can run while the others are working in the background. This tool is much more manual and requires a decent understanding of the Windows operating system as well as the malware you’re hunting. Prior to scanning, we want to ensure that Addition.txt is checked under Optional Scan. Everything under Whitelist should be checked as well:
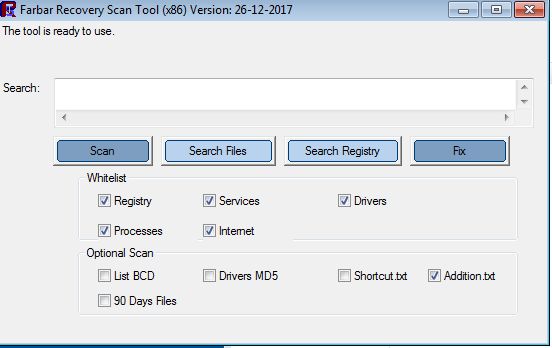
Once it finishes scanning we’ll find that it creates FRST.txt and Addition.txt in the same directory it is running from. Now that we have those reports, go ahead and create a fixlist.txt in the same location. We want to open up all of these files and sort of split our screen in half long ways, with FRST’s logs stacked on top of each other on top and our fixlist on bottom:

Now we navigate each of FRST’s logs line-by-line searching for anything known to be unwanted. FRST provides a large amount of information such as items whitelisted in Windows, all files created in the last 30-days, temporary internet files, proxy settings, user accounts, scheduled tasks, detected Alternate Data Streams, and event log entries. As we find items, we will copy that entire line and paste it into our fixlist. Basically any entry that contains a [No File], [X] or ATTENTION! can be removed, as well as anything believed to be associated with our infection. Thanks to Process Explorer, we know the exact location of our unwanted program. FRST will also help us find anything related to the program that isn’t running from the same directory as its parent process. Each section in FRST will tell you exactly what will happen to any entries if included in the fixlist. Once we think we’ve gotten everything, we want to add one last line to the fixlist with the contents of EmptyTemp:. This will go through and clear out everything in all temp folders (in case it wasn’t obvious). Be sure you save your fixlist now or you’ll have to repeat this time-consuming process. By the end of it, your fixlist will probably look something like this:

Now that we’ve got our fixlist, let’s go ahead and check on our other tools. JRT will just spit out a log when it finishes, while Adwcleaner will prompt you to manually clean everything it’s found. Prior to doing so, allow MBAR to finish as Adwcleaner will kill all running programs prior to cleaning up. Once MBAR is done, we can allow Adwcleaner to clean up, but read the prompts carefully. Depending on your version of Adwcleaner it will display a number of prompts, the last one stating it will reboot the computer. Ignore that prompt for now and go ahead and launch FRST one last time. Now that we’ve got our fixlist, click Fix and let it do its thing. Once it has completed, go ahead and reboot. Upon logging back in, we’ll find a Fixlog detailing exactly what FRST was able to remove.
Now if we run Autoruns and ProcEx we find that the process is no longer running and its autorun task has been removed!

















Comments